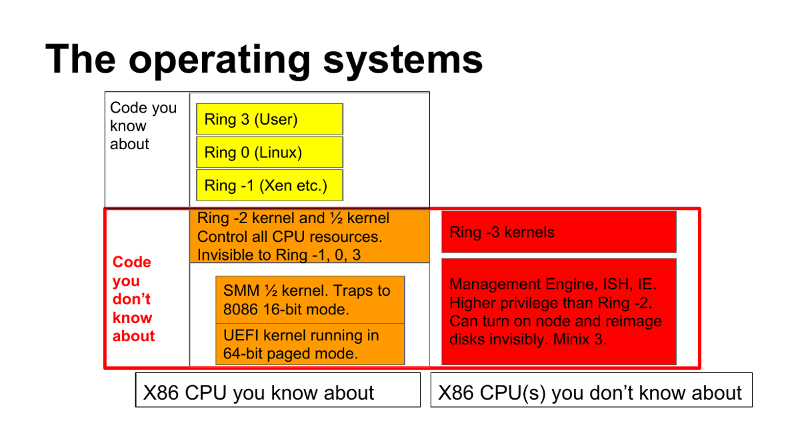
Disabling the Intel Management Engine
The Intel Management Engine (‘IME’ or ‘ME’) is an out-of-band co-processor integrated in all post-2006 Intel-CPU-based PCs. It has full network and memory access and runs proprietary, signed, closed-source software at ring -3, independently of the BIOS, main CPU and platform operating system — a fact which many regard as an unacceptable security risk (particularly given that at least one remotely exploitable security hole has already been reported). - EFI Install Guide / HN
In this mini-guide, I’ll run through the process of disabling the IME on your target PC.[10] To do so, we will use Nicola Corna’s me_cleaner. This software operates on the firmware stored in your PC’s BIOS chip (where the bulk of the ME’s code resides), and does two things:
- sets the ‘High Assurance Program’ bit, an ME ‘kill switch’ that the US government reportedly had incorporated for PCs used in sensitive applications;
- removes the vast majority of the ME’s software modules (including network stack, RTOS and Java VM), leaving only the essential ‘bring up’ components (the latter being necessary because, on modern systems, if the IME fails to initialize, either the machine startup will be completely halted at that point, or startup will appear to complete, only for a watchdog timer to reset the whole PC 30 minutes later[14]).
This combined ‘belt-and-braces’ approach means that the ME ought to cleanly enter a self-induced null state (after resetting the 30-minute watchdog timer) but, should that not work, it will nevertheless enter a failed state shortly thereafter (as the majority of its core software modules have been purged).
Replacing x86 firmware with Linux and Go
Today there are at least two and a half kernels between Linux and the hardware. Those kernels are proprietary and, not surprisingly, exploit friendly. They run at a higher privilege level than Linux and can manipulate both the hardware and the operating system in various ways. Worse yet, exploits can be written into the flash of the system so that they persist and are difficult or impossible to remove—shredding the motherboard is likely the only way out.